The aircraft carriers, underwater vehicles, or missile systems no longer determine the modern naval power. The speed of data, network resilience, and cybersecurity equally influence it nowadays. The United States Navy has one of the most complicated digital ecosystems in the world, linked to ships, aircraft, submarines, command centers, satellites, and allied forces worldwide.
The key equilibrium in this ecosystem is that, on the one hand, there is high-speed internet and communications, but on the other, there is strong cybersecurity. Rush and insecurity beckon doom. Operational effectiveness is impacted by security without speed limits. The Navy has to learn to do both–at the same time.
This paper will discuss the collaboration between cybersecurity high speed internet us navy activities, the importance of those in the strategic context, the technologies, the threats, and how the Navy is preparing to ensure the new era of digital warfare.
The importance of a High-Speed Internet in current naval operations.
The U.S Navy does not need high-speed connectivity to aid its operation–it is a mission requirement. Naval forces are distributed and experience rapidly moving and high-risk environments where the loss of lives or missions can be a result of delays in the transmission of data.
Onboard-Decision-Making in Real-Time.
Communication officers are guided by perpetual feeds of information:
- Radar, sonar, and drone sensor feeds.
- Intelligence reports and satellite images.
- Maintenance and logistics information.
- Meteorological and oceanographic models.
The fast networks enable the commanders to assess the threats, synchronize the forces as well as implementing the decisions in real time. Any delay of a few seconds in the detection of a threat or response can result in a tipping point in disputed waters.
Network-Centric Warfare
The idea of network-centric warfare, in which information superiority creates combat superiority has long been an idea held in the Navy. Ships, aircraft, and command centers are digitally connected to create one operational picture.
This is achievable through high-bandwidth communication, as they allow:
- Share targeting information immediately.
- Co-operate with the Air Force, Army, and Marines.
- Unify allied and NATO systems safely.
- This model of operation fails without a quick and efficient connection.
- The Cybersecurity Imperative: Why Fast is a Dangerous Thing.
Speed is a potent thing–but a fatal one without armour. All the high-speed connections are also potential attack surfaces.
The Navy as a Top Cyber Target.
The U.S Navy is a target of high value to:
- Nation-state adversaries
- Advanced persistent threats (APTs).
- Cyber espionage groups
- Supply-chain attackers
Naval systems are loaded with sensitive intelligence, plans of action, weapons, and personnel. A successful intrusion may reveal sensitive capabilities or deterrence strategy.
Cyber Threats within the Naval Environments.
There are cyber threats to the naval networks:
- Lateral movement and network intrusion.
- Viruses in software patches.
- GPS spoofing and signal interference.
- Communications link denial-of-service attacks.
- Analogies and manifested credentials.
The issue of recovering cyber incidents at sea is made more difficult by the fact that connectivity alternatives are scarce and access is prohibited.
A Case Study on how the U.S. Navy is Developing Secure High-speed Networks.
In a bid to address these challenges, the Navy develops its networks in a way that security is incorporated at each level and not as a post-implementation undertaking.
Defense-in-Depth Architecture
The naval networks are based on a defense-in-depth strategy:
- Firewalls, intrusion detection systems (perimeter defenses).
- Segmentation of the network to reduce the impact of the breach.
- Powerful data encryption on transit and at rest.
- Ongoing monitoring and integration of threat intelligence.
This layer defense strategy is such that one aspect of defense does not work; the rest does.
Secure Large Scale Communications.
Navy communication at high speed is dependent on high-speed encryption:
- Cryptography of satellite links is military-grade.
- There is an end-to-end encryption between ship-to-ship and ship-to-aircraft data exchanges.
- Secure key management is used to guarantee that only authorized systems communicate.
- Even during the interception of transmission, sensitive data is safeguarded through encryption.
Satellite Internet and Naval Cybersecurity
The satellite internet has emerged as a key facilitator or enabler of today’s naval operations, and it has changed the way fleets convey information, navigate, and carry out cyber operations across the expansive and, in most cases, remote maritime space. Satellite-based connectivity in comparison with terrestrial networks has the advantage of providing continuous and global coverage, allowing naval ships to keep secure command-and-control connections, share real-time intelligence, and coordinate operations even at the open ocean. This reliance on satellite internet, however, creates major cybersecurity obstacles to the naval forces as well. The use of satellite communications in naval networks by naval organizations, both with onboard combat systems, sensors, and logistics platforms, increases the attack surface available to cyber adversaries. Risk agents might seek to use the weaknesses in satellite connections by intercepting signals, jamming, spoofing, or hacking of ground sites and network administration frameworks.
An effective cyber attack may disrupt the navigation systems, deteriorate the situational awareness, disclose classified information, or even disrupt the weapon control systems, which is critically disastrous operationally and strategically. As a result, cybersecurity plans by the Navy ought to focus on the protection of the satellite internet infrastructure by ensuring that there is strong encryption, a protocol based on proper authentication of data, as well as constantly monitoring network traffic in search of irregularities. There is also a need for redundancy and resilience, and the navies are adopting the use of multi-orbit satellite architecture, backup communication networks, and quick recovery systems to maintain continuity in cases of cyber attacks or kinetic activities.
The Future of Naval Network Security Zero Trust.
Zero Trust is fast defining the future of the naval network security as the maritime forces deal with more advanced cyber threats in highly competitive operational theaters. The zero trust approach is based on the principle of never trust and always verify, in contrast to traditional perimeter-based security models in which the internal network has been assumed as a trusted environment. Zero trust requires constant authentication and authorization of every user, device, and system accessing naval networks. It is particularly critical in the case of modern navies since ships, submarines, aircraft, and shore-based facilities are inter-linked in intricate, distributed networks that in many cases utilize satellite and wireless communications.
Zero trust contributes to resilience by limiting the cross-domain movement in networks such that, even when an attacker hacks one of their parts, they cannot gain access to key combat, navigation, or intelligence systems. Zero-trust deployment in the naval context of the future will heavily utilize artificial intelligence, behavioral analytics, and automated policy enforcement to dynamically change security control in response to risk and operational conditions.
Cloud Computing: Sea Clouds: Speed vs Security.
Cloud computing on the sea is redefining the operations of the navy and maritime in the world as it integrates high-speed data processing with leading security services in the most hostile environments of the world. Historically, shipping was based on inflexible, hardware-intensive systems that restricted the flexibility and speed of decision-making. Maritime cloud architectures (including the private and tactical edge clouds onboard ships and the hybrid connections to the data centers on the shore) provide faster data exchange, real-time analytics, and better situational awareness today. This velocity enables commanders to digest sensor and intelligence reports as well as logistics information more effectively to aid fast and knowledgeable operational decision-making. Nevertheless, the work with cloud systems at sea also requires strict security since the connection is not always available, it depends on the use of satellite connections, and there is the possibility of cyber and electronic attacks.
In order to overcome such risks, maritime cloud services focus on powerful encryption and identity-based accessibility, sustained observation, and the principles of zero-trust, which guarantee verification of all requests irrespective of the location. Edge computing also ensures more security and resilience by enabling critical applications to operate locally even in the absence of central networks.
Naval cyberspace and Cyber Command.
Cybersecurity high speed internet us navy has become the core of the contemporary cyber naval operations, coordinating, defending, and, in case of necessity, projecting power into the cyber sphere of maritime conflicts. The cyber operations have become as important as the conventional sea, air, or undersea capabilities, as the naval platforms are becoming more and more networked. The role of Naval Cyber Command is to protect critical networks, which facilitate command and control, navigation, weapons systems, logistics, and intelligence to the fleets and shore installations. In addition to defense, cyber operations also allow navies to pursue offensive and intelligence-directed missions, including interference with enemy communications, sabotage of surveillance systems, and information environment shaping in support of maritime missions.
The success of any naval cyber operations depends on the tightly coupled relation with kinetic forces, as any cyber actions during joint and combined operations are synchronized with physical operations. It needs very professional personnel, new equipment to detect and respond to threats, and strict regulations of engagement in cyberspace. The cyber threats are changing very fast, and to keep the situation under awareness, Cyber Command should also prioritize continuous adaptation, the use of artificial intelligence, automation, and real-time analytics.
Related: Health threetrees com vn
Supply Chain Security: The Defence of What Bonds the Network.
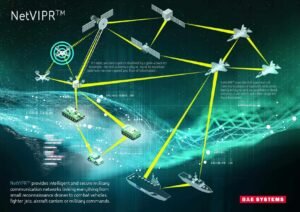
The fast networks rely on the hardware and software based on complicated supply chains around the world.
The importance of Supply Chain Security.
One weak point can:
- Plant backdoor vulnerabilities.
- Allow tenacious access by attackers.
- Defraud whole systems.
- The Navy is cautious in procurement and vetting of the vendor.
Measures to Reduce Risk
Key strategies include:
- Trusted supplier programs
- Checking of hardware and software.
- Constant checking of abnormalities.
- Navy cybersecurity has become part of supply chain security.
Preparing Sailors to Fight in the Digital Battlespace
It does not rely solely on technology. The human beings are the most powerful and the powerless.
Hacktivism on the Strengths of Collaboration.
- The Navy invests heavily in:
- Training of all personnel
- <|human|>Training of cyberspace hygiene.
- Cyber professionals education.
- Mimic exercises on cyber incidents.
- The programs minimize human error and enhance the readiness to respond.
Building a Cyber-Savvy Force
Through the incorporation of cybersecurity awareness into the routine of the Navy, the Navy ensures that both speed and security do not go against each other, but rather, they go hand in hand.
- Cyber Defense Automation and Artificial Intelligence.
- Manual defense cannot be used as networks get faster and more complicated.
AI-Driven Threat Detection
AI and machine learning help the Navy to:
- Identify malicious activities on the network.
- Detect possible intrusions sooner.
- Automate the preliminary response measures.
- Automation assists in maintaining the current of data that is high-speed.
- Striking a Balance between Automation and Control.
Although AI makes the defense process faster, human control is also necessary. The Navy takes the task of specially balancing automation and command authority to prevent unintended consequences.
Resilience and Redundancy: Readiness for the worst.

No system is invulnerable. The Navy creates its networks in such a manner that they can survive an attack and keep on functioning.
Built-In Redundancy
Naval networks include:
- There are several communication channels.
- Backup satellites and links
- Backup mechanisms of crucial processes.
- In case of failure of one connection, others assume the roles.
- Cyber Resiliency as a Strategic Benefit.
Strong networks do not give easy victories to the enemy. The Navy can remain effective in its operation even in an attack, which is a major deterrent in modern warfare.
International Business and Safe Connectivity.
- The U.S Navy does not work in isolation very often.
- Protective Information Exchange with Partners.
- Fast networks are simple to build, high-speed networks, and they are secure networks.
- Cooperation with other navies.
- Sharing of intelligence in real time.
- Harmonized responses to the international threats.
Interoperability is a must-have, but one should consider cybersecurity issues that can also be handled only with caution.
The Naval Cyber Domain: Threats on the Horizon.
The threat environment is in constant development.
Quantum Computing Risks
Potential future quantum technologies can:
- Breach conventional encryption.
- Dictate new cryptographic standards.
- The Navy is already studying post-quantum cryptography to be ahead of the game.
Gray-Zone and Hybrid Cyber Attacks.
The enemies act within the borders of a war less and less:
- Continuous network investigation.
- Information warfare
- Influence operations made possible by cyber.
Fast and safe network systems are supportive in tracking and preventing them at the earliest stage.
The Cyber-Secure Speed is Strategically Important.
Cybersecurity high speed internet us navy are neither technical nor technical specifications, it is strategic enablers.
Information Superiority as Navy Power.
The ability to:
- Collect information faster
- Secure it more effectively
- Act on it decisively
- characterizes naval supremacy in the cyber era.
- Intimidation with Computer Cavalry.
A Navy characterized by resilient, secure, and high-speed networks does not even encourage enemies to attempt to disrupt the cyber world.
The future of America: the Future of the U.S. Navy.
The future of the U.S. Navy is characterized by modernization, strategic competition, technological innovations, and adaptation to the quickly changing global security environment. The key feature of plans is a powerful drive towards modernization and building up of fleet; the 2026 proposal on the defense budget suggests financing 19 new battle force vessels, including submarines, destroyers, amphibious ships, and intelligence platforms. Concurrently, there are still long-standing shipbuilding issues and considerable investments into restructuring old shipyards to increase the production capacities and remain prepared are underway.
Wrapping Up
The convergence of cybersecurity and high-speed internet characterizes the U.S Navy operating, fighting, and deterring threats in the 21 st century. Speed enables action. Security preserves trust. They constitute the electronic backbone of contemporary naval power.
Technological superiority of the opponent will be the driving factor as the Navy will secure its networks and keep its connection unmatched. In the modern battlefield, bytes fly as quickly as missiles- and protecting them is as important as defending missiles.
Frequently Asked Questions (FAQs)
- What is cybersecurity’s role in the U.S. Navy?
Cybersecurity protects naval networks, weapons systems, communications, and sensitive data from cyber threats, ensuring mission readiness, operational security, and information superiority in modern warfare.
- How fast is the internet on U.S. Navy ships?
Internet speeds on U.S. Navy ships vary by mission and location but typically range from limited bandwidth for general use to higher-speed, priority connections for operational and command systems via satellite communications.
- Which military branch is best for cybersecurity?
All U.S. military branches have strong cybersecurity programs, but the U.S. Cyber Command integrates efforts across services, while the Navy, Air Force, and Army each excel in cyber operations aligned with their specific missions.


QQ88 là nhà cái cá cược trực tuyến uy tín, cung cấp casino live, nổ hũ, bắn cá và thể thao với trải nghiệm mượt, bảo mật cao.
QQ88 là nhà cái trực tuyến uy tín hàng đầu đông Nam Á, mang đến kho game hay ho và hấp dẫn: Casino ,bắn cá, đá gà, nổ hũ,… tặng 88k khi đăng ký và tặng 999k khi nạp đầu
QQ88 là nền tảng cá cược trực tuyến uy tín, tích hợp casino, nổ hũ, bắn cá và thể thao với trải nghiệm ổn định. Trải nghiệm giải trí online tại QQ88 với kho game đa dạng, giao diện thân thiện và thao tác nhanh gọn.
QQ88 là nền tảng cá cược trực tuyến uy tín, cung cấp casino, nổ hũ, bắn cá và thể thao với trải nghiệm ổn định, bảo mật cao.
QQ88 là cổng game cá cược trực tuyến uy tín, tích hợp casino live, nổ hũ, bắn cá và thể thao với trải nghiệm ổn định.
sex trẻ em dưới 10 tuổi
QQ88 là nền tảng cá cược trực tuyến uy tín, cung cấp casino live, nổ hũ, bắn cá và thể thao với hệ thống vận hành ổn định.
QQ88 là nền tảng cá cược trực tuyến uy tín, cung cấp casino live, nổ hũ, bắn cá và thể thao với hệ thống bảo mật cao, vận hành ổn định.
QQ88 là nền tảng giải trí trực tuyến với casino, thể thao, nổ hũ, bắn cá đa dạng. Hệ thống ổn định, dễ chơi, ưu đãi hấp dẫn cho người tham gia.
QQ88 là nền tảng cá cược trực tuyến uy tín, tích hợp casino live, nổ hũ, bắn cá và thể thao với trải nghiệm ổn định.
QQ88 là nền tảng cá cược trực tuyến uy tín, tích hợp casino live, nổ hũ, bắn cá và thể thao với trải nghiệm ổn định.
QQ88 là nền tảng cá cược trực tuyến uy tín, cung cấp casino live, nổ hũ, bắn cá và thể thao, bảo mật cao, thanh toán nhanh, trải nghiệm ổn định.
QQ88 là nền tảng cá cược trực tuyến uy tín, tích hợp casino live, nổ hũ, bắn cá và thể thao với trải nghiệm ổn định.
QQ88 mang đến hệ sinh thái cá cược trực tuyến toàn diện, nổi bật với casino live, slot đổi thưởng, bắn cá và thể thao ổn định.
Nhà cái QQ88 nổi bật với kho game phong phú, vận hành mượt mà và dịch vụ hỗ trợ người chơi liên tục.
QQ88 mang đến hệ sinh thái cá cược toàn diện, phù hợp cho cả người chơi mới và người chơi lâu năm.
QQ88 là cổng truy cập chính thức giúp người dùng tiếp cận hệ sinh thái giải trí trực tuyến ổn định, giao diện mượt và trải nghiệm an toàn.
QQ88 mang đến nền tảng cá cược online chuyên nghiệp, tối ưu tốc độ truy cập, giao diện mượt mà và trải nghiệm minh bạch cho người dùng.
QQ88 là nền tảng giải trí online được tối ưu trải nghiệm, giúp người dùng truy cập nhanh, thao tác mượt và tận hưởng dịch vụ ổn định lâu dài.
QQ88 đóng vai trò như cổng kết nối chính thức, hỗ trợ người dùng tiếp cận hệ sinh thái cá cược trực tuyến an toàn và hiệu quả.
QQ88 mang đến trải nghiệm giải trí trực tuyến linh hoạt, giao diện thân thiện, tốc độ tải nhanh và hệ thống vận hành minh bạch.
QQ88 cung cấp nền tảng giải trí online hiện đại, tối ưu thao tác người dùng và đảm bảo trải nghiệm liền mạch trên nhiều thiết bị.
QQ88 mang đến nền tảng giải trí trực tuyến tối ưu trải nghiệm, chú trọng hiệu quả vận hành và sự thoải mái trong mỗi lần đăng nhập.
QQ88 là cổng truy cập giải trí trực tuyến ổn định, tối ưu tốc độ tải, giao diện mượt và trải nghiệm liền mạch cho người dùng.
**mitolyn**
Mitolyn is a carefully developed, plant-based formula created to help support metabolic efficiency and encourage healthy, lasting weight management.
QQ88 cung cấp môi trường giải trí online hiện đại, dễ thao tác, giao diện mượt và khả năng vận hành ổn định.
QQ88 mang đến cổng truy cập giải trí online hiện đại, tập trung vào hiệu suất, giao diện thân thiện và tính tiện lợi lâu dài.
QQ88 cung cấp môi trường giải trí online hiện đại, tối ưu hiệu suất và đảm bảo trải nghiệm liền mạch khi sử dụng.
How are you?
QQ88 là nhà cái uytin 2026 , mang đến casino, thể thao, bắn cá, nổ hũ,…. Tham gia nhận 88K trải nghiệm
QQ88 là nhà cái uytin 2026 , mang đến casino, thể thao, bắn cá, nổ hũ,…. Tham gia nhận 88K trải nghiệm
QQ88 trang 1 google.com.vn
QQ88 là cổng truy cập giải trí trực tuyến ổn định, hỗ trợ người dùng tiếp cận hệ sinh thái game đa dạng với giao diện mượt, tốc độ nhanh và trải nghiệm liền mạch.
QQ88 là nền tảng giải trí online tối ưu toàn diện, giúp người dùng thao tác nhanh, hạn chế gián đoạn và tận hưởng dịch vụ ổn định lâu dài.
ình vào bằng Link fly88 thấy ổn định, không bị lỗi chuyển hướng.
QQ88 mang đến nền tảng giải trí trực tuyến được tối ưu hiệu suất, giúp người dùng truy cập nhanh, thao tác mượt và trải nghiệm ổn định.
QQ88 là nền tảng giải trí trực tuyến uy tín, tối ưu tốc độ truy cập, giao diện mượt và trải nghiệm ổn định cho người dùng.
QQ88 cung cấp nền tảng giải trí trực tuyến ổn định, tập trung vào tốc độ truy cập, giao diện thân thiện và trải nghiệm liền mạch.
QQ88 LAF NHAF QQ88 là nền tảng giải trí trực tuyến tối ưu tốc độ, giao diện mượt và mang lại trải nghiệm ổn định cho người dùng.
QQ88 cung cấp cổng truy cập giải trí online hiện đại, vận hành liền mạch và thuận tiện trên nhiều thiết bị.
QQ88 là cổng truy cập giải trí trực tuyến ổn định, tối ưu tốc độ tải, giao diện thân thiện và trải nghiệm mượt mà cho người dùng.
QQ88 cung cấp nền tảng giải trí trực tuyến ổn định, tối ưu trải nghiệm người dùng với giao diện mượt và khả năng truy cập nhanh.
QQ88 cung cấp cổng truy cập giải trí online hiện đại, hỗ trợ đa thiết bị, vận hành mượt mà và đảm bảo sự thuận tiện khi sử dụng.
QQ88 là nền tảng giải trí trực tuyến uy tín, tối ưu tốc độ truy cập, giao diện thân thiện và mang đến trải nghiệm ổn định cho người dùng.
Chơi bên FLY88 mấy hôm nay, tỷ lệ kèo ok phết.
QQ88 là nền tảng giải trí trực tuyến uy tín, tối ưu tốc độ truy cập, giao diện mượt và trải nghiệm ổn định cho người dùng.
QQ88 cung cấp cổng truy cập giải trí online hiện đại, vận hành liền mạch, hỗ trợ đa thiết bị và dễ sử dụng.
QQ88 là nền tảng giải trí trực tuyến uy tín, tối ưu trải nghiệm với tốc độ truy cập nhanh và giao diện thân thiện.
QQ88 mang đến cổng truy cập giải trí online hiện đại, vận hành ổn định và đảm bảo sự thuận tiện cho người dùng.
QQ88 là nhà cái hấp dẫn hàng đầu 2026 qq88gs.com là tên miền chính thức của nhà cái . Đăng ký ngay hôm nay nhận ngày ưu đãi ngập tràn
QQ88 là nhà cái hấp dẫn hàng đầu 2026 qq88gs.com là tên miền chính thức của nhà cái . Đăng ký ngay hôm nay nhận ngày ưu đãi ngập tràn
QQ88 là cổng truy cập giải trí trực tuyến được tối ưu hiệu suất, giúp người dùng thao tác nhanh và trải nghiệm ổn định.
QQ88 cung cấp cổng truy cập giải trí online hiện đại, hỗ trợ đa thiết bị, vận hành liền mạch và thuận tiện khi sử dụng.
QQ88 mang đến cổng truy cập giải trí online hiện đại, giao diện thân thiện và vận hành mượt mà trên nhiều thiết bị.
QQ88 cung cấp nền tảng giải trí online hiện đại, hỗ trợ đa thiết bị và đảm bảo vận hành liền mạch khi sử dụng.
QQ88 là cổng truy cập giải trí trực tuyến tối ưu tốc độ, giao diện mượt và mang lại trải nghiệm ổn định cho người dùng.
QQ88 là nền tảng giải trí trực tuyến được tối ưu hiệu suất, giúp người dùng truy cập nhanh và trải nghiệm ổn định.
QQ88 được xây dựng như một cổng truy cập ổn định và linh hoạt, chú trọng hiệu suất vận hành và sự thoải mái trong từng lần đăng nhập.
QQ88 được định hình như một không gian giải trí trực tuyến tối ưu hiệu suất, nơi trải nghiệm truy cập nhanh và sự ổn định luôn được đặt lên hàng đầu.